As a system administrator, you’re responsible for more than just uptime — you’re also the gatekeeper of your infrastructure’s security. One of the most effective yet often overlooked tools in your toolbox is the Linux firewall. It acts as the first line of defense between your systems and the wild internet.
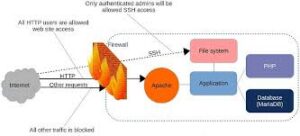
Two of the most widely used Linux firewall tools are Firewalld and UFW (Uncomplicated Firewall). While they both serve the same goal — managing network access — they do so in different ways, catering to different environments and skill levels.
This post will help you understand the difference, choose the right one for your environment, and know what ports to open, restrict, or block to stay secure.
🔐 Why Every Linux Server Needs a Proper Firewall Policy
- ✅ Reduce Attack Surface
Open ports are invitations for attackers. A firewall ensures only essential ports are accessible, reducing risk. - ✅ Prevent Lateral Movement
Host-based firewalls contain intrusions and prevent attackers from jumping between systems. - ✅ Meet Compliance Requirements
Compliance standards like ISO 27001, PCI-DSS, and HIPAA require network access control. - ✅ Apply Zero Trust Principles
Enforce least-privilege networking with host firewalls. - ✅ Add Defense in Depth
A firewall can still block attacks even when apps are misconfigured.
🔍 What Is Firewalld?
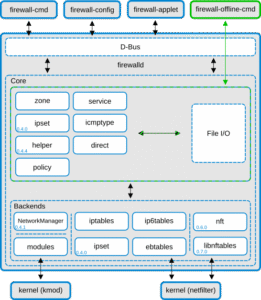
Firewalld is a dynamic firewall manager that sits on top of iptables or nftables. It organizes rules using zones and supports advanced configurations using rich rules.
- CLI:
firewall-cmd - Supports zones (e.g., internal, dmz, public)
- Dynamic changes without restart
- GUI via
firewall-config - Default on RHEL, CentOS, Fedora, Rocky Linux
![]()
🔍 What Is UFW?
UFW (Uncomplicated Firewall) is a user-friendly wrapper around iptables, great for simpler setups or less experienced users.
- CLI:
ufw - Simple syntax (
ufw allow 22/tcp) - IPv4 and IPv6 support
- GUI available via GUFW
- Default on Ubuntu and Debian
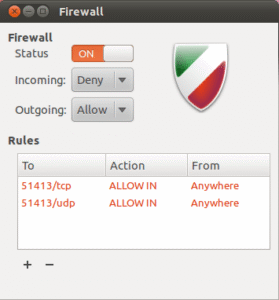
⚙️ Firewalld vs UFW: Feature Comparison
| Feature | Firewalld | UFW |
|---|---|---|
| Default in | RHEL, CentOS, Fedora | Ubuntu, Debian |
| Backend | iptables / nftables | iptables |
| Zones Support | ✅ Yes | ❌ No |
| Rich Rules | ✅ Yes | ❌ No |
| Dynamic Changes | ✅ Yes | ❌ No |
| Command Syntax | Verbose (firewall-cmd) | Simple (ufw) |
| GUI | ✅ firewall-config | ✅ GUFW |
| IPv6 Support | ✅ | ✅ |
| Enterprise Features | ✅ Advanced | ❌ Basic |
| Learning Curve | Moderate | Easy |
🛠️ Real-World Use Cases
Choose UFW if:
- You need fast, minimal setup
- Managing a single VPS or cloud server
- You’re on Ubuntu or Debian
- You don’t need advanced features
Choose Firewalld if:
- Managing enterprise or production servers
- Need interface or zone-specific rules
- Use Cockpit or Zabbix
- Need live rule updates without restart
🧪 Basic Examples
# UFW: Allow SSH
sudo ufw allow 22/tcp
sudo ufw enable
sudo ufw status
# Firewalld: Allow SSH
sudo firewall-cmd --permanent --zone=public --add-service=ssh
sudo firewall-cmd --reload
sudo firewall-cmd --list-all
# Firewalld: Assign Interface to Zone
sudo firewall-cmd --zone=internal --change-interface=eth1 --permanent
📎 Bonus Tip: Mastering nftables and Port Management
Want even more control? Learn nftables — the modern, faster, and cleaner replacement for iptables. Both UFW and Firewalld can use it as a backend, but configuring it directly gives you full control for advanced scenarios.
🚪 Know Your Ports — What to Open, Restrict, or Close
✅ Common Ports to Open (If Needed)
| Port | Protocol | Service | Notes |
|---|---|---|---|
| 22 | TCP | SSH | Secure shell — restrict to admin IPs |
| 80 | TCP | HTTP | Public web traffic |
| 443 | TCP | HTTPS | Encrypted web traffic |
| 5432 | TCP | PostgreSQL | Restrict to app servers or VPN |
| 3306 | TCP | MySQL/MariaDB | Private subnet only |
| 25 | TCP | SMTP | Outbound only, restrict inbound |
| 161 | UDP | SNMP | Used by monitoring tools |
⚠️ Ports to Open with Restrictions
| Port | Protocol | Recommendations |
|---|---|---|
| 22 | TCP | Allow from VPN or trusted IP only |
| 5432 | TCP | App servers only |
| 3306 | TCP | Internal access only |
| 25 | TCP | Outbound relay only |
| 161 | UDP | Monitoring IPs only |
# Firewalld: Restrict PostgreSQL to one IP
firewall-cmd --permanent --add-rich-rule='rule family="ipv4" source address="10.0.0.100" port port="5432" protocol="tcp" accept'
🚫 Ports You Should Almost Always Close
| Port | Service | Reason |
|---|---|---|
| 23 | Telnet | Insecure, deprecated |
| 21 | FTP | Use SFTP/FTPS instead |
| 111 | RPCbind | Often targeted in exploits |
| 2049 | NFS | Internal use only |
| 445 | SMB | Block externally |
🧠 Final Thoughts
Whether you choose UFW for simplicity, Firewalld for flexibility, or nftables for performance — the goal is the same: limit exposure and control traffic intelligently.
- ✅ Keep rules minimal
- ✅ Audit regularly
- ✅ Allow only trusted traffic
Open only what you need. Block what you don’t. Review often.
Views: 302